Конфигуриране на Edge Router Lite на Ubiquiti Networks
http://www.ubnt.com/

От доста време насам чакам да внесат в България Edge Router Lite на фирмата Ubiquiti Networks. Рекламите и превютата са толкова впечатляващи че, човек няма как да не иска да го поразцъка. Естествено знам че, голяма част от цялата тази еуфория е реклама защото американците са добри в това, но устройство което струва около 100 долара тежи 300 грама и превърта милион пакети (според производителя) е найстина иновация на пазара.
Дойде денят в който държа в ръцете си Edge Router Lite. Като за начало мисля да го конфигурирам вкъщи въпреки че, многократно надхвърля възможностите за home router ако се представи добре ще го бодна в офиса където както конфигурацията така и трафика е доста по сериозен.
Преди още да го включа знам че, Edge Router Lite е с операционна система форк на Vyatta а аз много харесвам интерфейса и, но съм и малко притеснен тъй като познавам Ubiquiti как обичат да опростяват нещата да не са поорязали функционалноста на Vyatta.
Edge Router Lite има четири порта: console, 0, 1, 2. Конфигурирам си на лаптопа ип адрес 192.168.1.2 пъхам ЛАН кабела в порт 0 на Edge Router Lite и отварям през уеб http://192.168.1.1 Типично за продукти на Ubiquiti потребителя е:ubnt и паролата е:ubnt
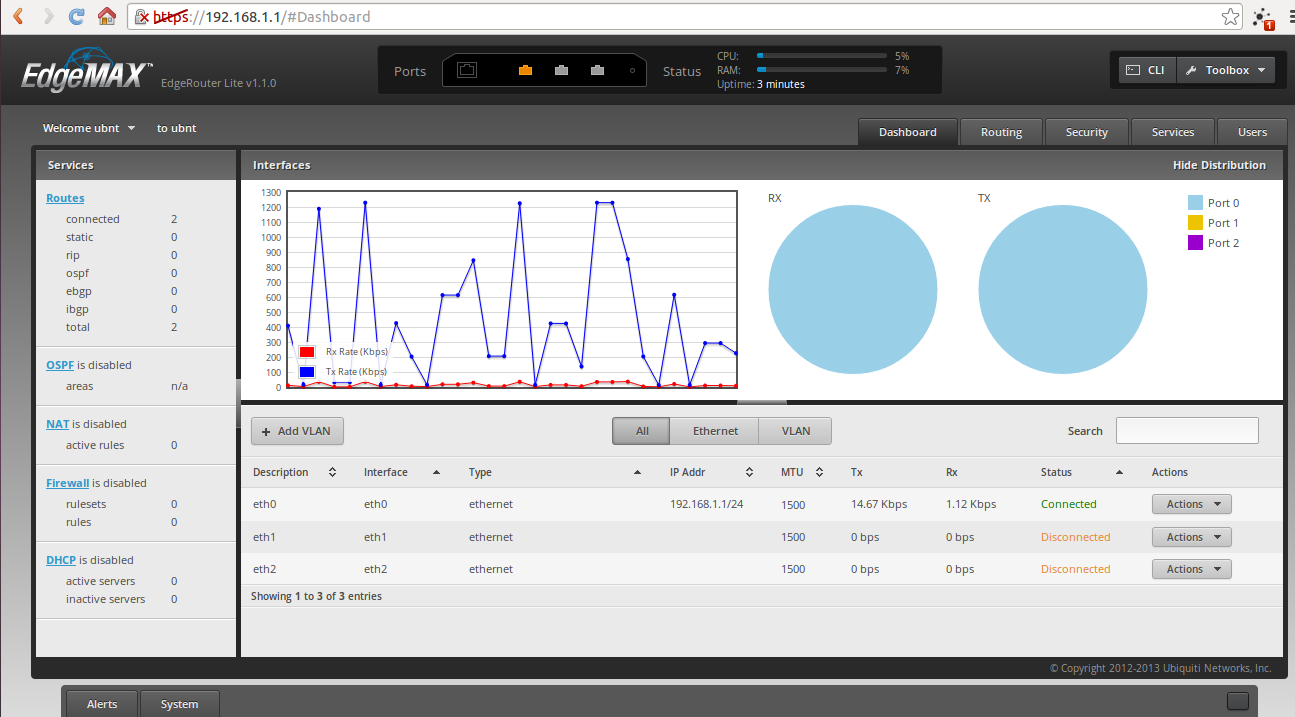
Да си призная честно след като видях уеб интерфейса останах малко замислен. Въобще не очаквах такъв постен мениджмънт но пък може и идеята да е такава по скоро мониторинг отколкото конфигурация. Но след като се логнах през SSH се поуспокоих, интерфейса си е 100% Vyatta.
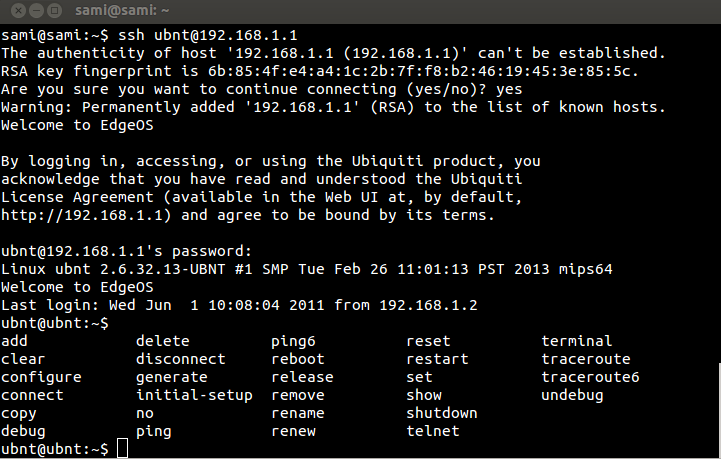
Терминала на Vyatta може в началото да ви се стори малко объркващ но всъщност е доста интуитивен (ще е лесен за тези които са работили с Juniper) Системата работи в два режима – user, веднага след логването сте в него и configure – в този режим се влиза с същата команда. В режим configure имаме следните команди:
ubnt@ubnt#
Possible completions:
confirm Confirm prior commit-confirm
comment Add comment to this configuration element
commit Commit the current set of changes
commit-confirm Commit the current set of changes with 'confirm' required
compare Compare configuration revisions
copy Copy a configuration element
delete Delete a configuration element
discard Discard uncommitted changes
edit Edit a sub-element
exit Exit from this configuration level
load Load configuration from a file and replace running configuration
loadkey Load user SSH key from a file
merge Load configuration from a file and merge running configuration
rename Rename a configuration element
rollback Rollback to a prior config revision (requires reboot)
run Run an operational-mode command
save Save configuration to a file
set Set the value of a parameter or create a new element
show Show the configuration (default values may be suppressed) |
ubnt@ubnt#
Possible completions:
confirm Confirm prior commit-confirm
comment Add comment to this configuration element
commit Commit the current set of changes
commit-confirm Commit the current set of changes with 'confirm' required
compare Compare configuration revisions
copy Copy a configuration element
delete Delete a configuration element
discard Discard uncommitted changes
edit Edit a sub-element
exit Exit from this configuration level
load Load configuration from a file and replace running configuration
loadkey Load user SSH key from a file
merge Load configuration from a file and merge running configuration
rename Rename a configuration element
rollback Rollback to a prior config revision (requires reboot)
run Run an operational-mode command
save Save configuration to a file
set Set the value of a parameter or create a new element
show Show the configuration (default values may be suppressed)
Най важното засега което трябва да знаем е че, със:
set – създаваме правила
delete – изтриваме правила
discard – отказваме правило преди да е влязло в сила
commit – правилата който сме създали със set ще влязат в сила но няма да важат след рестарт
save – правилата който са в сила ще важат и след рестарт
show – показване на конфигурацията
exit – излизане от текущия режим
И така нека да преминем към самата конфигурация. Тъй като на практика имаме три порта 0, 1, 2 а ние сме влезли през 0 ще използвам за WAN порт 2 а 0 и 1 ще ги конфигурирам в bridge за да мога в 0 да бодна едно AP (Access Point) да имам безжичен достъп и в 1 ще включа един суич за локалните ми компютри.
Конфигуриране на LAN (в Bridge на port 0 и 1)
set interfaces bridge br0 address 192.168.1.1/24
set interfaces ethernet eth0 bridge-group bridge br0
set interfaces ethernet eth1 bridge-group bridge br0 |
set interfaces bridge br0 address 192.168.1.1/24
set interfaces ethernet eth0 bridge-group bridge br0
set interfaces ethernet eth1 bridge-group bridge br0
Конфигуриране на WAN и default gateway
set interfaces ethernet eth2 address 10.125.3.2/24
set protocols static route 0.0.0.0/0 next-hop 10.125.3.1 |
set interfaces ethernet eth2 address 10.125.3.2/24
set protocols static route 0.0.0.0/0 next-hop 10.125.3.1
Конфигуриране на DNS сървъри
set system name-server 93.155.131.1
set system name-server 93.155.130.14 |
set system name-server 93.155.131.1
set system name-server 93.155.130.14
Конфигуриране на локален кеширащ DNS сървър
set service dns forwarding system
set service dns forwarding listen-on br0 |
set service dns forwarding system
set service dns forwarding listen-on br0
Конфигуриране на DHCP сървър
set service dhcp-server shared-network-name HOME subnet 192.168.1.0/24 default-router 192.168.1.1
set service dhcp-server shared-network-name HOME subnet 192.168.1.0/24 dns-server 192.168.1.1
set service dhcp-server shared-network-name HOME subnet 192.168.1.0/24 domain-name HOME-ROUTER
set service dhcp-server shared-network-name HOME subnet 192.168.1.0/24 start 192.168.1.10 stop 192.168.1.20 |
set service dhcp-server shared-network-name HOME subnet 192.168.1.0/24 default-router 192.168.1.1
set service dhcp-server shared-network-name HOME subnet 192.168.1.0/24 dns-server 192.168.1.1
set service dhcp-server shared-network-name HOME subnet 192.168.1.0/24 domain-name HOME-ROUTER
set service dhcp-server shared-network-name HOME subnet 192.168.1.0/24 start 192.168.1.10 stop 192.168.1.20
Конфигуриране на NAT (masquerade)
set service nat rule 5000 source address 192.168.1.0/24
set service nat rule 5000 outbound-interface eth2
set service nat rule 5000 type masquerade |
set service nat rule 5000 source address 192.168.1.0/24
set service nat rule 5000 outbound-interface eth2
set service nat rule 5000 type masquerade
Конфигуриране на UPNP
set service upnp listen-on br0 outbound-interface eth2 |
set service upnp listen-on br0 outbound-interface eth2
В общи линии до тук ние сглобихме един домашен рутер с елементарна конфигурация като такъв можем да си купим от всеки един магазин при това много по ефтино. Но това което не можем да правим с ефтин рутер е управление на трафика и по сериозно конфигуриране на правилата в защитната стена (firewall).
Конфигуриране на трафик контрол по ип адрес
set traffic-policy limiter UPLOAD default bandwidth 1000mbit
set traffic-policy limiter UPLOAD class 10 bandwidth 10mbit
set traffic-policy limiter UPLOAD class 10 match user ip source address 192.168.1.10/32
set traffic-policy limiter UPLOAD class 11 bandwidth 10mbit
set traffic-policy limiter UPLOAD class 11 match user ip source address 192.168.1.11/32
set traffic-policy limiter UPLOAD class 12 bandwidth 10mbit
set traffic-policy limiter UPLOAD class 12 match user ip source address 192.168.1.12/32
set traffic-policy limiter UPLOAD class 13 bandwidth 10mbit
set traffic-policy limiter UPLOAD class 13 match user ip source address 192.168.1.13/32
set traffic-policy limiter UPLOAD class 14 bandwidth 10mbit
set traffic-policy limiter UPLOAD class 14 match user ip source address 192.168.1.14/32
set traffic-policy limiter UPLOAD class 15 bandwidth 10mbit
set traffic-policy limiter UPLOAD class 15 match user ip source address 192.168.1.15/32
set interfaces bridge br0 traffic-policy in UPLOAD |
set traffic-policy limiter UPLOAD default bandwidth 1000mbit
set traffic-policy limiter UPLOAD class 10 bandwidth 10mbit
set traffic-policy limiter UPLOAD class 10 match user ip source address 192.168.1.10/32
set traffic-policy limiter UPLOAD class 11 bandwidth 10mbit
set traffic-policy limiter UPLOAD class 11 match user ip source address 192.168.1.11/32
set traffic-policy limiter UPLOAD class 12 bandwidth 10mbit
set traffic-policy limiter UPLOAD class 12 match user ip source address 192.168.1.12/32
set traffic-policy limiter UPLOAD class 13 bandwidth 10mbit
set traffic-policy limiter UPLOAD class 13 match user ip source address 192.168.1.13/32
set traffic-policy limiter UPLOAD class 14 bandwidth 10mbit
set traffic-policy limiter UPLOAD class 14 match user ip source address 192.168.1.14/32
set traffic-policy limiter UPLOAD class 15 bandwidth 10mbit
set traffic-policy limiter UPLOAD class 15 match user ip source address 192.168.1.15/32
set interfaces bridge br0 traffic-policy in UPLOAD
set traffic-policy shaper DOWNLOAD bandwidth 1000mbit
set traffic-policy shaper DOWNLOAD default bandwidth 100%
set traffic-policy shaper DOWNLOAD class 10 bandwidth 10mbit
set traffic-policy shaper DOWNLOAD class 10 match USER ip destination address 192.168.1.10/32
set traffic-policy shaper DOWNLOAD class 11 bandwidth 10mbit
set traffic-policy shaper DOWNLOAD class 11 match USER ip destination address 192.168.1.11/32
set traffic-policy shaper DOWNLOAD class 12 bandwidth 10mbit
set traffic-policy shaper DOWNLOAD class 12 match USER ip destination address 192.168.1.12/32
set traffic-policy shaper DOWNLOAD class 13 bandwidth 10mbit
set traffic-policy shaper DOWNLOAD class 13 match USER ip destination address 192.168.1.13/32
set traffic-policy shaper DOWNLOAD class 14 bandwidth 10mbit
set traffic-policy shaper DOWNLOAD class 14 match USER ip destination address 192.168.1.14/32
set traffic-policy shaper DOWNLOAD class 15 bandwidth 10mbit
set traffic-policy shaper DOWNLOAD class 15 match USER ip destination address 192.168.1.15/32
set interfaces bridge br0 traffic-policy out DOWNLOAD |
set traffic-policy shaper DOWNLOAD bandwidth 1000mbit
set traffic-policy shaper DOWNLOAD default bandwidth 100%
set traffic-policy shaper DOWNLOAD class 10 bandwidth 10mbit
set traffic-policy shaper DOWNLOAD class 10 match USER ip destination address 192.168.1.10/32
set traffic-policy shaper DOWNLOAD class 11 bandwidth 10mbit
set traffic-policy shaper DOWNLOAD class 11 match USER ip destination address 192.168.1.11/32
set traffic-policy shaper DOWNLOAD class 12 bandwidth 10mbit
set traffic-policy shaper DOWNLOAD class 12 match USER ip destination address 192.168.1.12/32
set traffic-policy shaper DOWNLOAD class 13 bandwidth 10mbit
set traffic-policy shaper DOWNLOAD class 13 match USER ip destination address 192.168.1.13/32
set traffic-policy shaper DOWNLOAD class 14 bandwidth 10mbit
set traffic-policy shaper DOWNLOAD class 14 match USER ip destination address 192.168.1.14/32
set traffic-policy shaper DOWNLOAD class 15 bandwidth 10mbit
set traffic-policy shaper DOWNLOAD class 15 match USER ip destination address 192.168.1.15/32
set interfaces bridge br0 traffic-policy out DOWNLOAD
Шейпърчето си работи доволно.
Важно е да се знае че, във веригите DOWNLOAD ип адресите който не са описани в ограничението на скороста ползват най ниската скорост общо. Макар това в случая да е 10mbit (default bandwidth 100%). По тази причина трябва да се опишат всички ип адреси, група от адреси или мрежи във веригите download. В противен случай всички останали ще споделят 10mbit !!!
Правила forwarding в защитната стена
Тъй като в DHCP сървъра аз разреших само на десет хоста да получават ип адреси искам само те да имат Интернет и ако някой участник в мрежата си конфигурира ръчно адрес освен от тези десет да няма достъп през рутера. Затова аз ще ги опиша в група защото групата се явява само едно правило в защитната стена на рутера и по този начин намалява натоварването му спрямо случая ако бяха десет правила например.
set firewall group address-group IP-ACCEPT-FORWARDING address 192.168.1.10
set firewall group address-group IP-ACCEPT-FORWARDING address 192.168.1.11
set firewall group address-group IP-ACCEPT-FORWARDING address 192.168.1.12
set firewall group address-group IP-ACCEPT-FORWARDING address 192.168.1.13
set firewall group address-group IP-ACCEPT-FORWARDING address 192.168.1.14
set firewall group address-group IP-ACCEPT-FORWARDING address 192.168.1.15
set firewall group address-group IP-ACCEPT-FORWARDING address 192.168.1.16
set firewall group address-group IP-ACCEPT-FORWARDING address 192.168.1.17
set firewall group address-group IP-ACCEPT-FORWARDING address 192.168.1.18
set firewall group address-group IP-ACCEPT-FORWARDING address 192.168.1.19
set firewall group address-group IP-ACCEPT-FORWARDING address 192.168.1.20
set firewall name DROP-FORWARD default-action drop
set firewall name DROP-FORWARD rule 10 action accept
set firewall name DROP-FORWARD rule 10 source group address-group IP-ACCEPT-FORWARDING
set interfaces bridge br0 firewall in name DROP-FORWARD |
set firewall group address-group IP-ACCEPT-FORWARDING address 192.168.1.10
set firewall group address-group IP-ACCEPT-FORWARDING address 192.168.1.11
set firewall group address-group IP-ACCEPT-FORWARDING address 192.168.1.12
set firewall group address-group IP-ACCEPT-FORWARDING address 192.168.1.13
set firewall group address-group IP-ACCEPT-FORWARDING address 192.168.1.14
set firewall group address-group IP-ACCEPT-FORWARDING address 192.168.1.15
set firewall group address-group IP-ACCEPT-FORWARDING address 192.168.1.16
set firewall group address-group IP-ACCEPT-FORWARDING address 192.168.1.17
set firewall group address-group IP-ACCEPT-FORWARDING address 192.168.1.18
set firewall group address-group IP-ACCEPT-FORWARDING address 192.168.1.19
set firewall group address-group IP-ACCEPT-FORWARDING address 192.168.1.20
set firewall name DROP-FORWARD default-action drop
set firewall name DROP-FORWARD rule 10 action accept
set firewall name DROP-FORWARD rule 10 source group address-group IP-ACCEPT-FORWARDING
set interfaces bridge br0 firewall in name DROP-FORWARD
Логично по същия начин ще забраня Windows share в двете посоки.
set firewall group port-group PORT-DROP-FORWARDING port 137-139
set firewall group port-group PORT-DROP-FORWARDING port 445
set firewall name DROP-PORT-FORWARD rule 11 action drop
set firewall name DROP-PORT-FORWARD rule 11 protocol tcp_udp
set firewall name DROP-PORT-FORWARD rule 11 source group port-group PORT-DROP-FORWARDING
set firewall name DROP-PORT-FORWARD rule 12 action drop
set firewall name DROP-PORT-FORWARD rule 12 protocol tcp_udp
set firewall name DROP-PORT-FORWARD rule 12 destination group port-group PORT-DROP-FORWARDING
set interfaces bridge br0 firewall in name DROP-PORT-FORWARD |
set firewall group port-group PORT-DROP-FORWARDING port 137-139
set firewall group port-group PORT-DROP-FORWARDING port 445
set firewall name DROP-PORT-FORWARD rule 11 action drop
set firewall name DROP-PORT-FORWARD rule 11 protocol tcp_udp
set firewall name DROP-PORT-FORWARD rule 11 source group port-group PORT-DROP-FORWARDING
set firewall name DROP-PORT-FORWARD rule 12 action drop
set firewall name DROP-PORT-FORWARD rule 12 protocol tcp_udp
set firewall name DROP-PORT-FORWARD rule 12 destination group port-group PORT-DROP-FORWARDING
set interfaces bridge br0 firewall in name DROP-PORT-FORWARD
Правила port forwarding в NAT
Често се налага да позлвам remote desktop у нас затова ще си отворя порт 3389 и ще го насоча към локалния ип адрес 192.168.1.10
set service nat rule 10 inbound-interface eth2
set service nat rule 10 destination address 10.125.3.2
set service nat rule 10 destination port 3389
set service nat rule 10 inside-address address 192.168.1.10
set service nat rule 10 inside-address port 3389
set service nat rule 10 protocol tcp
set service nat rule 10 type destination |
set service nat rule 10 inbound-interface eth2
set service nat rule 10 destination address 10.125.3.2
set service nat rule 10 destination port 3389
set service nat rule 10 inside-address address 192.168.1.10
set service nat rule 10 inside-address port 3389
set service nat rule 10 protocol tcp
set service nat rule 10 type destination
Правила INPUT в защитната стена
Има разни ип адреси който ме дразнят, някой хвърлят спам, дуги сканират а трети се опитват да налучкат паролата ми. По тази причина ще ги дропнна за да не ме виждат.
set firewall group address-group IP-DROP-INPUT address 10.125.3.5
set firewall group address-group IP-DROP-INPUT address 10.125.3.10
set firewall group address-group IP-DROP-INPUT address 10.125.3.11
set firewall group address-group IP-DROP-INPUT address 93.155.130.12
set firewall name DROP-INPUT default-action accept
set firewall name DROP-INPUT rule 13 action drop
set firewall name DROP-INPUT rule 13 source group address-group IP-DROP-INPUT
set interfaces ethernet eth2 firewall local name DROP-INPUT |
set firewall group address-group IP-DROP-INPUT address 10.125.3.5
set firewall group address-group IP-DROP-INPUT address 10.125.3.10
set firewall group address-group IP-DROP-INPUT address 10.125.3.11
set firewall group address-group IP-DROP-INPUT address 93.155.130.12
set firewall name DROP-INPUT default-action accept
set firewall name DROP-INPUT rule 13 action drop
set firewall name DROP-INPUT rule 13 source group address-group IP-DROP-INPUT
set interfaces ethernet eth2 firewall local name DROP-INPUT
Разбира се имаме възможност да забраняваме и портове от страна на WAN интерфейса на рутера.
set firewall group port-group PORT-DROP-INPUT port 53
set firewall group port-group PORT-DROP-INPUT port 843
set firewall name DROP-INPUT rule 14 action drop
set firewall name DROP-INPUT rule 14 protocol tcp_udp
set firewall name DROP-INPUT rule 14 destination group port-group PORT-DROP-INPUT |
set firewall group port-group PORT-DROP-INPUT port 53
set firewall group port-group PORT-DROP-INPUT port 843
set firewall name DROP-INPUT rule 14 action drop
set firewall name DROP-INPUT rule 14 protocol tcp_udp
set firewall name DROP-INPUT rule 14 destination group port-group PORT-DROP-INPUT
SNMP Мониторинг
Тъй като искам MRTG и Cacti да ми чертаят графика през snmp от отдалечена машина прилагам следните правила.
set service snmp community public authorization ro
set service snmp community public client 93.155.130.13
set service snmp contact support@itservice-bg.net
set service snmp location Bulgaria |
set service snmp community public authorization ro
set service snmp community public client 93.155.130.13
set service snmp contact support@itservice-bg.net
set service snmp location Bulgaria
Конфигуриране на име и времева зона
Името обаче ще се промени след като излезем и се логнем наново в рутера.
set system host-name home
set system time-zone Europe/Sofia |
set system host-name home
set system time-zone Europe/Sofia
Смяна на паролата
set system login user ubnt authentication plaintext-password "паролата" |
set system login user ubnt authentication plaintext-password "паролата"
Мониторинг
Както мениджмънта така и мониторинга през уеб интерфейс е доста постен а едно от най важните качества на високия клас рутер освен стандартните ping и traceroute е наблюдение на трафика и процесите в него. В самият мониторинг на рутера няма нужда да сте в режим configure. Всъщност ако сте в режим configure трябва да се добави run пред show, например ubnt@home# run show interfaces
резулата е:
ubnt@home# run show interfaces
Codes: S - State, L - Link, u - Up, D - Down, A - Admin Down
Interface IP Address S/L Description
--------- ---------- --- -----------
br0 192.168.1.1/24 u/u
eth0 - u/u
eth1 - u/u
eth2 10.125.3.2/24 u/u
lo 127.0.0.1/8 u/u
::1/128 |
ubnt@home# run show interfaces
Codes: S - State, L - Link, u - Up, D - Down, A - Admin Down
Interface IP Address S/L Description
--------- ---------- --- -----------
br0 192.168.1.1/24 u/u
eth0 - u/u
eth1 - u/u
eth2 10.125.3.2/24 u/u
lo 127.0.0.1/8 u/u
::1/128
Рутираща таблица
ubnt@home:~$ show ip route
Codes: K - kernel route, C - connected, S - static, R - RIP, O - OSPF,
I - ISIS, B - BGP, > - selected route, * - FIB route
S>* 0.0.0.0/0 [1/0] via 10.125.3.1, eth2
C>* 10.125.3.0/24 is directly connected, eth2
C>* 127.0.0.0/8 is directly connected, lo
C>* 192.168.1.0/24 is directly connected, br0 |
ubnt@home:~$ show ip route
Codes: K - kernel route, C - connected, S - static, R - RIP, O - OSPF,
I - ISIS, B - BGP, > - selected route, * - FIB route
S>* 0.0.0.0/0 [1/0] via 10.125.3.1, eth2
C>* 10.125.3.0/24 is directly connected, eth2
C>* 127.0.0.0/8 is directly connected, lo
C>* 192.168.1.0/24 is directly connected, br0
Наблюдение на DHCP сървъра
ubnt@home:~$ show dhcp leases
IP address Hardware Address Lease expiration Pool Client Name
---------- ---------------- ---------------- ---- -----------
192.168.1.10 f0:4d:a2:86:ef:70 2013/07/09 20:45:22 HOME sami
192.168.1.11 00:22:fb:5d:21:8e 2013/07/10 06:49:21 HOME sami
192.168.1.12 00:26:9e:31:8b:29 2013/07/10 05:55:02 HOME Eli-PC
192.168.1.13 00:a0:d1:a0:c5:be 2013/07/10 03:08:43 HOME CECI-PC
192.168.1.14 00:1c:23:95:39:08 2013/07/10 03:38:49 HOME |
ubnt@home:~$ show dhcp leases
IP address Hardware Address Lease expiration Pool Client Name
---------- ---------------- ---------------- ---- -----------
192.168.1.10 f0:4d:a2:86:ef:70 2013/07/09 20:45:22 HOME sami
192.168.1.11 00:22:fb:5d:21:8e 2013/07/10 06:49:21 HOME sami
192.168.1.12 00:26:9e:31:8b:29 2013/07/10 05:55:02 HOME Eli-PC
192.168.1.13 00:a0:d1:a0:c5:be 2013/07/10 03:08:43 HOME CECI-PC
192.168.1.14 00:1c:23:95:39:08 2013/07/10 03:38:49 HOME
Наблюдение на NAT правила
ubnt@home:~$ show nat rules
Type Codes: SRC - source, DST - destination, MASQ - masquerade
X at the front of rule implies rule is excluded
rule type intf translation
---- ---- ---- -----------
10 DST eth2 daddr 10.125.3.2 to 192.168.1.10
proto-tcp dport 3389 to 3389
5000 MASQ eth2 saddr 192.168.1.0/24 to 10.125.3.2
proto-all sport ANY |
ubnt@home:~$ show nat rules
Type Codes: SRC - source, DST - destination, MASQ - masquerade
X at the front of rule implies rule is excluded
rule type intf translation
---- ---- ---- -----------
10 DST eth2 daddr 10.125.3.2 to 192.168.1.10
proto-tcp dport 3389 to 3389
5000 MASQ eth2 saddr 192.168.1.0/24 to 10.125.3.2
proto-all sport ANY
Наблюдение на NAT конекции
ubnt@home# run show nat translations
Pre-NAT src Pre-NAT dst Post-NAT src Post-NAT dst
192.168.1.12:50320 84.40.66.158:58182 10.125.3.2:50320 84.40.66.158:58182
udp: snat: 192.168.1.12 ==> 10.125.3.2 timeout: 142 use: 2
192.168.1.12:54317 10.0.0.2:59614 10.125.3.2:54317 10.0.0.2:59614
udp: snat: 192.168.1.12 ==> 10.125.3.2 timeout: 26 use: 2
192.168.1.12:51744 77.85.126.55:64453 10.125.3.2:51744 77.85.126.55:64453
tcp: snat: 192.168.1.12 ==> 10.125.3.2 timeout: 3 use: 2
192.168.1.12:54317 79.131.129.91:64164 10.125.3.2:54317 79.131.129.91:64164
udp: snat: 192.168.1.12 ==> 10.125.3.2 timeout: 28 use: 2
192.168.1.12:50939 66.171.231.38:443 10.125.3.2:50939 66.171.231.38:443
tcp: snat: 192.168.1.12 ==> 10.125.3.2 timeout: 7188 use: 2
192.168.1.12:51772 91.201.172.105:1710 10.125.3.2:51772 91.201.172.105:1710
tcp: snat: 192.168.1.12 ==> 10.125.3.2 timeout: 20 use: 2
192.168.1.12:51837 78.83.97.87:17764 10.125.3.2:51837 78.83.97.87:17764
tcp: snat: 192.168.1.12 ==> 10.125.3.2 timeout: 50 use: 2
192.168.1.12:50320 186.221.174.198:7186 10.125.3.2:50320 186.221.174.198:7186
udp: snat: 192.168.1.12 ==> 10.125.3.2 timeout: 6 use: 2 |
ubnt@home# run show nat translations
Pre-NAT src Pre-NAT dst Post-NAT src Post-NAT dst
192.168.1.12:50320 84.40.66.158:58182 10.125.3.2:50320 84.40.66.158:58182
udp: snat: 192.168.1.12 ==> 10.125.3.2 timeout: 142 use: 2
192.168.1.12:54317 10.0.0.2:59614 10.125.3.2:54317 10.0.0.2:59614
udp: snat: 192.168.1.12 ==> 10.125.3.2 timeout: 26 use: 2
192.168.1.12:51744 77.85.126.55:64453 10.125.3.2:51744 77.85.126.55:64453
tcp: snat: 192.168.1.12 ==> 10.125.3.2 timeout: 3 use: 2
192.168.1.12:54317 79.131.129.91:64164 10.125.3.2:54317 79.131.129.91:64164
udp: snat: 192.168.1.12 ==> 10.125.3.2 timeout: 28 use: 2
192.168.1.12:50939 66.171.231.38:443 10.125.3.2:50939 66.171.231.38:443
tcp: snat: 192.168.1.12 ==> 10.125.3.2 timeout: 7188 use: 2
192.168.1.12:51772 91.201.172.105:1710 10.125.3.2:51772 91.201.172.105:1710
tcp: snat: 192.168.1.12 ==> 10.125.3.2 timeout: 20 use: 2
192.168.1.12:51837 78.83.97.87:17764 10.125.3.2:51837 78.83.97.87:17764
tcp: snat: 192.168.1.12 ==> 10.125.3.2 timeout: 50 use: 2
192.168.1.12:50320 186.221.174.198:7186 10.125.3.2:50320 186.221.174.198:7186
udp: snat: 192.168.1.12 ==> 10.125.3.2 timeout: 6 use: 2
Наблюдение правилата на защитната стена
ubnt@home:~$ show firewall statistics
--------------------------------------------------------------------------------
IPv4 Firewall "DROP-FORWARD"
Inactive - Not applied to any interfaces or zones.
rule packets bytes action description
---- ------- ----- ------ -----------
10 5793 982775 ACCEPT
10000 194 14808 DROP DEFAULT ACTION
--------------------------------------------------------------------------------
IPv4 Firewall "DROP-INPUT"
Active on (eth2,LOCAL)
rule packets bytes action description
---- ------- ----- ------ -----------
13 2 168 DROP
14 0 0 DROP
10000 11577 1623621 ACCEPT DEFAULT ACTION
--------------------------------------------------------------------------------
IPv4 Firewall "DROP-PORT-FORWARD"
Active on (br0,IN)
rule packets bytes action description
---- ------- ----- ------ -----------
11 132 18318 DROP
12 32 1920 DROP
10000 577820 84108759 ACCEPT DEFAULT ACTION |
ubnt@home:~$ show firewall statistics
--------------------------------------------------------------------------------
IPv4 Firewall "DROP-FORWARD"
Inactive - Not applied to any interfaces or zones.
rule packets bytes action description
---- ------- ----- ------ -----------
10 5793 982775 ACCEPT
10000 194 14808 DROP DEFAULT ACTION
--------------------------------------------------------------------------------
IPv4 Firewall "DROP-INPUT"
Active on (eth2,LOCAL)
rule packets bytes action description
---- ------- ----- ------ -----------
13 2 168 DROP
14 0 0 DROP
10000 11577 1623621 ACCEPT DEFAULT ACTION
--------------------------------------------------------------------------------
IPv4 Firewall "DROP-PORT-FORWARD"
Active on (br0,IN)
rule packets bytes action description
---- ------- ----- ------ -----------
11 132 18318 DROP
12 32 1920 DROP
10000 577820 84108759 ACCEPT DEFAULT ACTION
Стандартни Линукс команди
Важно е да се знае, че Vyatta все пак е Debian базирана Линукс дистрибуция и под удобния терминален интерфейс се намират всички демони и инструменти за един Линукс рутер като ping, traceroute, ifconfig, ip route, iptables, conntrack, ipset, pptpd, squid3, tcpdump, upnpd, pppoe и др. Но за да проверим правилата в iptables трябва да добавим sudo преди командата:
ubnt@home# sudo iptables -nvL -t nat
Chain PREROUTING (policy ACCEPT 7189 packets, 733K bytes)
pkts bytes target prot opt in out source destination
0 0 DNAT udp -- eth2 * 0.0.0.0/0 0.0.0.0/0 udp dpt:50320 to:192.168.1.12:50320
0 0 DNAT tcp -- eth2 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:50320 to:192.168.1.12:50320
106K 11M VYATTA_PRE_DNAT_HOOK all -- * * 0.0.0.0/0 0.0.0.0/0
2 88 DNAT tcp -- eth2 * 0.0.0.0/0 10.125.3.2 tcp dpt:3389 /* NAT-10 */ to:192.168.1.10:3389
Chain POSTROUTING (policy ACCEPT 1371 packets, 91715 bytes)
pkts bytes target prot opt in out source destination
80282 6793K VYATTA_PRE_SNAT_HOOK all -- * * 0.0.0.0/0 0.0.0.0/0
65746 5638K MASQUERADE all -- * eth2 192.168.1.0/24 0.0.0.0/0 /* NAT-5000 */
Chain OUTPUT (policy ACCEPT 396 packets, 39388 bytes)
pkts bytes target prot opt in out source destination
Chain VYATTA_PRE_DNAT_HOOK (1 references)
pkts bytes target prot opt in out source destination
106K 11M RETURN all -- * * 0.0.0.0/0 0.0.0.0/0
Chain VYATTA_PRE_SNAT_HOOK (1 references)
pkts bytes target prot opt in out source destination
80282 6793K RETURN all -- * * 0.0.0.0/0 0.0.0.0/0 |
ubnt@home# sudo iptables -nvL -t nat
Chain PREROUTING (policy ACCEPT 7189 packets, 733K bytes)
pkts bytes target prot opt in out source destination
0 0 DNAT udp -- eth2 * 0.0.0.0/0 0.0.0.0/0 udp dpt:50320 to:192.168.1.12:50320
0 0 DNAT tcp -- eth2 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:50320 to:192.168.1.12:50320
106K 11M VYATTA_PRE_DNAT_HOOK all -- * * 0.0.0.0/0 0.0.0.0/0
2 88 DNAT tcp -- eth2 * 0.0.0.0/0 10.125.3.2 tcp dpt:3389 /* NAT-10 */ to:192.168.1.10:3389
Chain POSTROUTING (policy ACCEPT 1371 packets, 91715 bytes)
pkts bytes target prot opt in out source destination
80282 6793K VYATTA_PRE_SNAT_HOOK all -- * * 0.0.0.0/0 0.0.0.0/0
65746 5638K MASQUERADE all -- * eth2 192.168.1.0/24 0.0.0.0/0 /* NAT-5000 */
Chain OUTPUT (policy ACCEPT 396 packets, 39388 bytes)
pkts bytes target prot opt in out source destination
Chain VYATTA_PRE_DNAT_HOOK (1 references)
pkts bytes target prot opt in out source destination
106K 11M RETURN all -- * * 0.0.0.0/0 0.0.0.0/0
Chain VYATTA_PRE_SNAT_HOOK (1 references)
pkts bytes target prot opt in out source destination
80282 6793K RETURN all -- * * 0.0.0.0/0 0.0.0.0/0
Или пък с tcpdump:
ubnt@home# sudo tcpdump -i eth2 -n
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth2, link-type EN10MB (Ethernet), capture size 65535 bytes
13:06:56.803501 ARP, Request who-has 212.233.179.16 tell 212.233.179.1, length 46
13:06:56.827025 ARP, Request who-has 10.125.3.11 tell 10.125.3.1, length 46
13:06:56.886605 IP 10.125.3.2.55856 > 173.252.102.241.443: Flags [.], ack 612259548, win 16128, length 0
13:06:57.052913 IP 10.125.3.2.54317 > 94.245.121.253.3544: UDP, length 56
13:06:57.053054 IP 10.125.3.2.54317 > 157.56.106.184.3544: UDP, length 56
13:06:57.207514 IP 94.245.121.253.3544 > 10.125.3.2.54317: UDP, length 56
13:06:57.208258 IP 10.125.3.2.54317 > 192.168.0.100.51906: UDP, length 52
13:06:57.208402 IP 10.125.3.2.54317 > 77.70.61.144.51906: UDP, length 52
13:06:57.213249 IP 77.76.178.94.2949 > 212.233.179.18.15732: Flags [S], seq 2812746257, win 65535, options [mss 1420,nop,nop,sackOK], length 0
13:06:57.229101 ARP, Request who-has 212.233.179.124 tell 212.233.179.1, length 46
13:06:57.237965 ARP, Request who-has 212.233.179.124 tell 212.233.179.1, length 46
13:06:57.244269 ARP, Request who-has 10.125.3.12 tell 10.125.3.1, length 46
13:06:57.257560 IP 94.245.121.253.3544 > 10.125.3.2.54317: UDP, length 56
13:06:57.258675 IP 10.125.3.2.54317 > 192.168.0.100.52508: UDP, length 52
13:06:57.258821 IP 10.125.3.2.54317 > 178.75.235.216.52508: UDP, length 52
13:06:57.282282 IP 78.182.236.174.52619 > 212.233.179.18.15732: Flags [S], seq 3761485222, win 14600, options [mss 1400,sackOK,TS val 7283081 ecr 0,nop,wscale 2], length 0
13:06:57.334762 ARP, Request who-has 212.233.179.124 tell 212.233.179.1, length 46
13:06:57.335150 IP 212.25.47.243.6319 > 212.233.179.18.15732: UDP, length 67
13:06:57.350380 IP 10.125.3.2.55856 > 173.252.102.241.443: Flags [P.], seq 0:1077, ack 1, win 16128, length 1077
^C
19 packets captured
19 packets received by filter
0 packets dropped by kernel |
ubnt@home# sudo tcpdump -i eth2 -n
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth2, link-type EN10MB (Ethernet), capture size 65535 bytes
13:06:56.803501 ARP, Request who-has 212.233.179.16 tell 212.233.179.1, length 46
13:06:56.827025 ARP, Request who-has 10.125.3.11 tell 10.125.3.1, length 46
13:06:56.886605 IP 10.125.3.2.55856 > 173.252.102.241.443: Flags [.], ack 612259548, win 16128, length 0
13:06:57.052913 IP 10.125.3.2.54317 > 94.245.121.253.3544: UDP, length 56
13:06:57.053054 IP 10.125.3.2.54317 > 157.56.106.184.3544: UDP, length 56
13:06:57.207514 IP 94.245.121.253.3544 > 10.125.3.2.54317: UDP, length 56
13:06:57.208258 IP 10.125.3.2.54317 > 192.168.0.100.51906: UDP, length 52
13:06:57.208402 IP 10.125.3.2.54317 > 77.70.61.144.51906: UDP, length 52
13:06:57.213249 IP 77.76.178.94.2949 > 212.233.179.18.15732: Flags [S], seq 2812746257, win 65535, options [mss 1420,nop,nop,sackOK], length 0
13:06:57.229101 ARP, Request who-has 212.233.179.124 tell 212.233.179.1, length 46
13:06:57.237965 ARP, Request who-has 212.233.179.124 tell 212.233.179.1, length 46
13:06:57.244269 ARP, Request who-has 10.125.3.12 tell 10.125.3.1, length 46
13:06:57.257560 IP 94.245.121.253.3544 > 10.125.3.2.54317: UDP, length 56
13:06:57.258675 IP 10.125.3.2.54317 > 192.168.0.100.52508: UDP, length 52
13:06:57.258821 IP 10.125.3.2.54317 > 178.75.235.216.52508: UDP, length 52
13:06:57.282282 IP 78.182.236.174.52619 > 212.233.179.18.15732: Flags [S], seq 3761485222, win 14600, options [mss 1400,sackOK,TS val 7283081 ecr 0,nop,wscale 2], length 0
13:06:57.334762 ARP, Request who-has 212.233.179.124 tell 212.233.179.1, length 46
13:06:57.335150 IP 212.25.47.243.6319 > 212.233.179.18.15732: UDP, length 67
13:06:57.350380 IP 10.125.3.2.55856 > 173.252.102.241.443: Flags [P.], seq 0:1077, ack 1, win 16128, length 1077
^C
19 packets captured
19 packets received by filter
0 packets dropped by kernel
В заключение бих казал че, Edge Router Lite ми харесва, макар и в случая да не му използвам възможностите като хардуер, главно от гледна точка на трафика който може да поддържа. Но Ubiquiti както очаквах все пак са орязали доста от функционалноста на Vyatta като WAN load balance, policy routing и failover което не го прави чак толкова висок клас от гледна точка на функционалност. Надявам се в следващата версия на firmware на Edge Router Lite на Ubiquiti Networks да променят това.
Конфигуриране на Edge Router Lite на Ubiquiti Networks





Досега някак си с насмешка гледах на напъните на убнт да направят рутер но след това четиво направо се замислих …