/routing bgp template
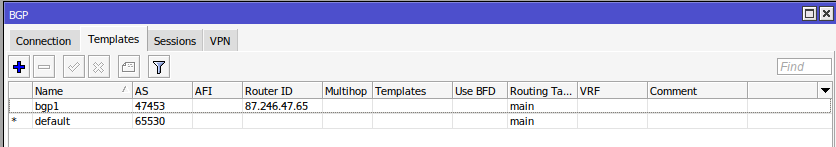
/routing bgp template
set default disabled=no output.network=bgp-networks
add as=47453 disabled=no name=bgp1 output.network=bgp-networks .redistribute=connected,static router-id=87.246.47.65 routing-table=main/routing bgp template
- Това е секцията за BGP шаблони (templates) в MikroTik.
- BGP шаблонът позволява повторно използване на настройки за различни BGP peer-ове.
set default disabled=no
- Активира (
disabled=no) default шаблона за BGP. - Това означава, че ако не е указан друг шаблон, ще се използва този.
output.network=bgp-networks
- Определя кои мрежи ще бъдат анонсирани към BGP peer-овете.
- В този случай
bgp-networksе списък с мрежи, дефиниран в/ip firewall address-list.
/routing bgp connection
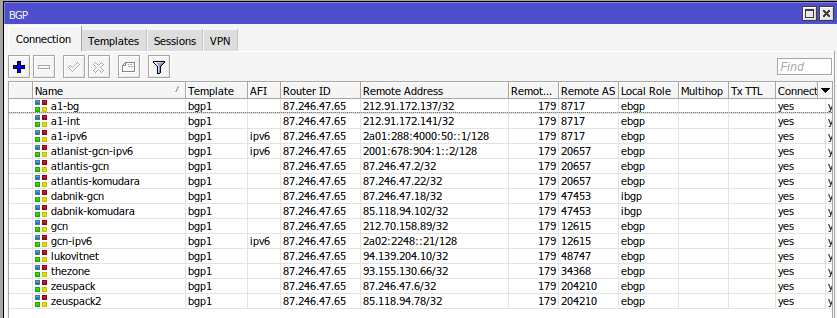
/routing bgp connection
add as=47453 cisco-vpls-nlri-len-fmt=auto-bits connect=yes disabled=no input.affinity=alone .filter=gcn-in listen=yes local.role=ebgp name=gcn output.affinity=alone .filter-chain=gcn-out .network=bgp-networks .redistribute=connected,static remote.address=212.70.158.89/32 \
.as=12615 .port=179 router-id=87.246.47.65 routing-table=main templates=bgp1
add as=47453 cisco-vpls-nlri-len-fmt=auto-bits connect=yes disabled=no input.affinity=alone .filter=thezone-in listen=yes local.role=ebgp name=thezone output.affinity=alone .filter-chain=thezone-out .network=bgp-networks .redistribute=connected,static remote.address=\
93.155.130.66/32 .as=34368 .port=179 router-id=87.246.47.65 routing-table=main templates=bgp1
add address-families=ipv6 as=47453 cisco-vpls-nlri-len-fmt=auto-bits connect=yes disabled=no input.affinity=alone .filter=gcn-ipv6-in listen=yes local.role=ebgp name=gcn-ipv6 output.affinity=alone .filter-chain=gcn-ipv6-out .network=bgp-networks .redistribute=\
connected,static remote.address=2a02:2248::21/128 .as=12615 .port=179 router-id=87.246.47.65 routing-table=main templates=bgp1
add as=47453 cisco-vpls-nlri-len-fmt=auto-bits connect=yes disabled=no input.affinity=alone .filter=a1-bg-in listen=yes local.role=ebgp name=a1-bg output.affinity=alone .filter-chain=a1-bg-out .network=bgp-networks .redistribute=connected,static remote.address=\
212.91.172.137/32 .as=8717 .port=179 router-id=87.246.47.65 routing-table=main templates=bgp1
add as=47453 cisco-vpls-nlri-len-fmt=auto-bits connect=yes disabled=no input.affinity=alone .filter=a1-int-in listen=yes local.role=ebgp name=a1-int output.affinity=alone .filter-chain=a1-int-out .network=bgp-networks .redistribute=connected,static remote.address=\
212.91.172.141/32 .as=8717 .port=179 router-id=87.246.47.65 routing-table=main templates=bgp1
add address-families=ipv6 as=47453 cisco-vpls-nlri-len-fmt=auto-bits connect=yes disabled=no input.affinity=alone .filter=a1-ipv6-in listen=yes local.role=ebgp name=a1-ipv6 output.affinity=alone .filter-chain=a1-ipv6-out .network=bgp-networks .redistribute=connected,static \
remote.address=2a01:288:4000:50::1/128 .as=8717 .port=179 router-id=87.246.47.65 routing-table=main templates=bgp1
add as=47453 cisco-vpls-nlri-len-fmt=auto-bits connect=yes disabled=no input.affinity=alone .filter=atlantis-gcn-in listen=yes local.role=ebgp name=atlantis-gcn output.affinity=alone .default-originate=always .filter-chain=atlantis-gcn-out .network=bgp-networks \
.redistribute=connected,static remote.address=87.246.47.2/32 .as=20657 .port=179 router-id=87.246.47.65 routing-table=main templates=bgp1
add address-families=ipv6 as=47453 cisco-vpls-nlri-len-fmt=auto-bits connect=yes disabled=no input.affinity=alone .filter=atlantis-gcn--ipv6-in listen=yes local.role=ebgp name=atlanist-gcn-ipv6 output.affinity=alone .filter-chain=atlantis-gcn-ipv6-out .network=bgp-networks \
.redistribute=connected,static remote.address=2001:678:904:1::2/128 .as=20657 .port=179 router-id=87.246.47.65 routing-table=main templates=bgp1
add as=47453 cisco-vpls-nlri-len-fmt=auto-bits connect=yes disabled=no input.affinity=alone .filter=zeuspack-in listen=yes local.role=ebgp name=zeuspack output.affinity=alone .default-originate=always .filter-chain=zeuspack-out .network=bgp-networks .redistribute=\
connected,static remote.address=87.246.47.6/32 .as=204210 .port=179 router-id=87.246.47.65 routing-table=main templates=bgp1
add as=47453 cisco-vpls-nlri-len-fmt=auto-bits connect=yes disabled=no input.affinity=alone .filter=lukovitnet-in listen=yes local.role=ebgp name=lukovitnet output.affinity=alone .default-originate=always .filter-chain=lukovitnet-out .network=bgp-networks .redistribute=\
connected,static remote.address=94.139.204.10/32 .as=48747 .port=179 router-id=87.246.47.65 routing-table=main templates=bgp1
add as=47453 cisco-vpls-nlri-len-fmt=auto-bits connect=yes disabled=no input.affinity=alone .filter=atlantis-komudara-in listen=yes local.role=ebgp name=atlantis-komudara output.affinity=alone .default-originate=always .filter-chain=atlantis-komudara-out .network=\
bgp-networks .redistribute=connected,static remote.address=87.246.47.22/32 .as=20657 .port=179 router-id=87.246.47.65 routing-table=main templates=bgp1
add as=47453 cisco-vpls-nlri-len-fmt=auto-bits connect=yes disabled=no input.affinity=alone .filter=zeuspack2-in listen=yes local.role=ebgp name=zeuspack2 output.affinity=alone .default-originate=always .filter-chain=zeuspack2-out .network=bgp-networks .redistribute=\
connected,static remote.address=85.118.94.78/32 .as=204210 .port=179 router-id=87.246.47.65 routing-table=main templates=bgp1
add as=47453 cisco-vpls-nlri-len-fmt=auto-bits connect=yes disabled=no input.affinity=alone .filter=dabnik-gcn-in listen=yes local.role=ibgp name=dabnik-gcn output.affinity=alone .default-originate=always .filter-chain=dabnik-gcn-out .network=bgp-networks .redistribute=\
connected,static remote.address=87.246.47.18/32 .as=47453 .port=179 router-id=87.246.47.65 routing-table=main templates=bgp1
add as=47453 cisco-vpls-nlri-len-fmt=auto-bits connect=yes disabled=no input.affinity=alone .filter=dabnik-komudara-in listen=yes local.role=ibgp name=dabnik-komudara output.affinity=alone .default-originate=always .filter-chain=dabnik-komudara-out .network=bgp-networks \
.redistribute=connected,static remote.address=85.118.94.102/32 .as=47453 .port=179 router-id=87.246.47.65 routing-table=main templates=bgp1
/routing bgp connection add
- Създава нова BGP сесия с конкретен peer.
as=47453
- Определя локалния AS номер на рутера.
- В този случай AS 47453 е твоята автономна система.
connect=yes
- Разрешава връзката към peer-а.
disabled=no
- Уверява се, че BGP сесията е активна.
input.affinity=alone / output.affinity=alone
- Управлява обработката на входящите/изходящите пакети за баланс на натоварването.
input.filter=gcn-in
- Определя входящия филтър, който контролира какви маршрути ще бъдат приети.
- В този случай
gcn-inфилтрира входящите маршрути.
output.filter-chain=gcn-out
- Определя изходящата филтърна верига, която контролира кои маршрути ще бъдат рекламирани към peer-а.
listen=yes
- Разрешава BGP peer-ът да приема връзки.
local.role=ebgp
- Дефинира ролята на тази BGP сесия като eBGP (връзка с друга автономна система).
- Ако стойността беше
ibgp, това би означавало вътрешна BGP връзка.
name=gcn
- Дава име на BGP сесията (
gcn), което е полезно за управление и диагностика.
output.network=bgp-networks
- Определя кои мрежи ще бъдат рекламирани.
bgp-networksсъдържа предварително дефинирани префикси от/ip firewall address-list.
redistribute=connected,static
- Позволява автоматично анонсиране на
connectedиstaticмаршрути.
remote.address=212.70.158.89/32
- Указва IP адреса на BGP peer-а (външния съсед).
remote.as=12615
- Определя AS номера на отдалечения BGP peer (в този случай AS 12615).
router-id=87.246.47.65
- Дефинира BGP Router ID, който обикновено е уникален за устройството.
routing-table=main
- Указва основната маршрутизираща таблица, в която ще бъдат добавени маршрутите.
templates=bgp1
- Използва конфигурацията на предварително създадения BGP шаблон
bgp1.
/routing filter rule
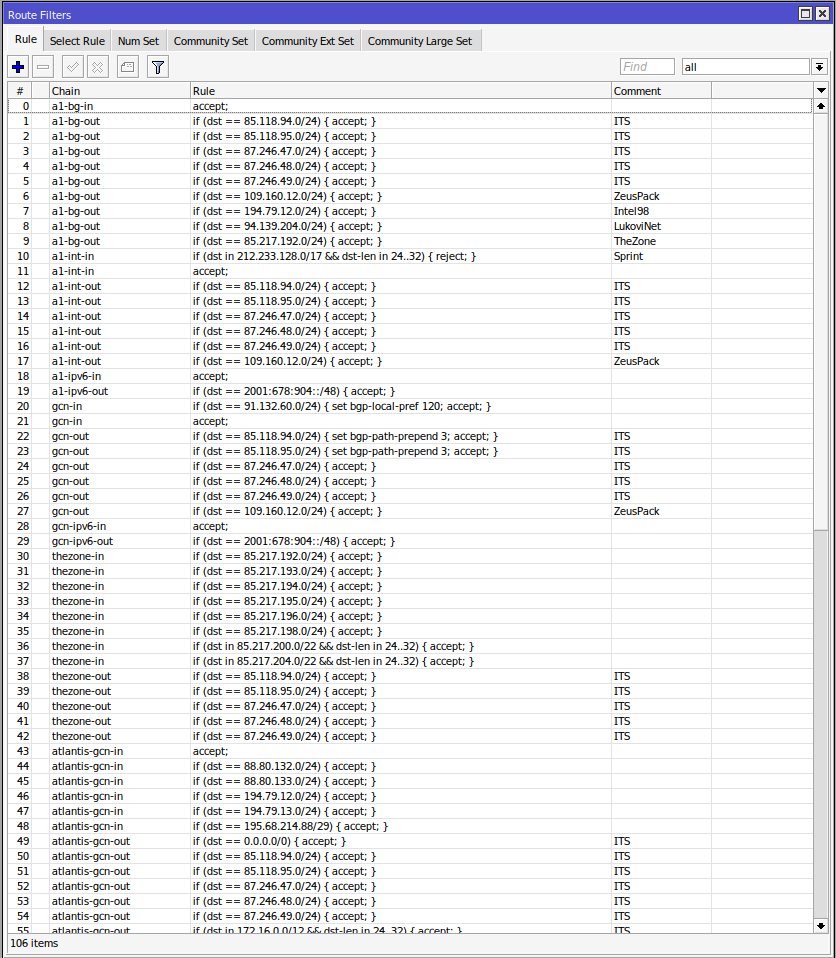
/routing filter rule
add chain=a1-bg-in disabled=no rule="accept;"
add chain=a1-bg-out comment=ITS disabled=no rule="if (dst == 85.118.94.0/24) { accept; }"
add chain=a1-bg-out comment=ITS disabled=no rule="if (dst == 85.118.95.0/24) { accept; }"
add chain=a1-bg-out comment=ITS disabled=no rule="if (dst == 87.246.47.0/24) { accept; }"
add chain=a1-bg-out comment=ITS disabled=no rule="if (dst == 87.246.48.0/24) { accept; }"
add chain=a1-bg-out comment=ITS disabled=no rule="if (dst == 87.246.49.0/24) { accept; }"
add chain=a1-bg-out comment=ZeusPack disabled=no rule="if (dst == 109.160.12.0/24) { accept; }"
add chain=a1-bg-out comment=Intel98 disabled=no rule="if (dst == 194.79.12.0/24) { accept; }"
add chain=a1-bg-out comment=LukoviNet disabled=no rule="if (dst == 94.139.204.0/24) { accept; }"
add chain=a1-bg-out comment=TheZone disabled=no rule="if (dst == 85.217.192.0/24) { accept; }"
add chain=a1-int-in comment=Sprint disabled=no rule="if (dst in 212.233.128.0/17 && dst-len in 24..32) { reject; }"
add chain=a1-int-in disabled=no rule="accept;"
add chain=a1-int-out comment=ITS disabled=no rule="if (dst == 85.118.94.0/24) { accept; }"
add chain=a1-int-out comment=ITS disabled=no rule="if (dst == 85.118.95.0/24) { accept; }"
add chain=a1-int-out comment=ITS disabled=no rule="if (dst == 87.246.47.0/24) { accept; }"
add chain=a1-int-out comment=ITS disabled=no rule="if (dst == 87.246.48.0/24) { accept; }"
add chain=a1-int-out comment=ITS disabled=no rule="if (dst == 87.246.49.0/24) { accept; }"
add chain=a1-int-out comment=ZeusPack disabled=no rule="if (dst == 109.160.12.0/24) { accept; }"
add chain=a1-ipv6-in disabled=no rule="accept;"
add chain=a1-ipv6-out disabled=no rule="if (dst == 2001:678:904::/48) { accept; }"
add chain=gcn-in disabled=no rule="if (dst == 91.132.60.0/24) { set bgp-local-pref 120; accept; }"
add chain=gcn-in disabled=no rule="accept;"
add chain=gcn-out comment=ITS disabled=no rule="if (dst == 85.118.94.0/24) { set bgp-path-prepend 3; accept; }"
add chain=gcn-out comment=ITS disabled=no rule="if (dst == 85.118.95.0/24) { set bgp-path-prepend 3; accept; }"
add chain=gcn-out comment=ITS disabled=no rule="if (dst == 87.246.47.0/24) { accept; }"
add chain=gcn-out comment=ITS disabled=no rule="if (dst == 87.246.48.0/24) { accept; }"
add chain=gcn-out comment=ITS disabled=no rule="if (dst == 87.246.49.0/24) { accept; }"
add chain=gcn-out comment=ZeusPack disabled=no rule="if (dst == 109.160.12.0/24) { accept; }"
add chain=gcn-ipv6-in disabled=no rule="accept;"
add chain=gcn-ipv6-out disabled=no rule="if (dst == 2001:678:904::/48) { accept; }"
add chain=thezone-in disabled=no rule="if (dst == 85.217.192.0/24) { accept; }"
add chain=thezone-in disabled=no rule="if (dst == 85.217.193.0/24) { accept; }"
add chain=thezone-in disabled=no rule="if (dst == 85.217.194.0/24) { accept; }"
add chain=thezone-in disabled=no rule="if (dst == 85.217.195.0/24) { accept; }"
add chain=thezone-in disabled=no rule="if (dst == 85.217.196.0/24) { accept; }"
add chain=thezone-in disabled=no rule="if (dst == 85.217.198.0/24) { accept; }"
add chain=thezone-in disabled=no rule="if (dst in 85.217.200.0/22 && dst-len in 24..32) { accept; }"
add chain=thezone-in disabled=no rule="if (dst in 85.217.204.0/22 && dst-len in 24..32) { accept; }"
add chain=thezone-out comment=ITS disabled=no rule="if (dst == 85.118.94.0/24) { accept; }"
add chain=thezone-out comment=ITS disabled=no rule="if (dst == 85.118.95.0/24) { accept; }"
add chain=thezone-out comment=ITS disabled=no rule="if (dst == 87.246.47.0/24) { accept; }"
add chain=thezone-out comment=ITS disabled=no rule="if (dst == 87.246.48.0/24) { accept; }"
add chain=thezone-out comment=ITS disabled=no rule="if (dst == 87.246.49.0/24) { accept; }"
add chain=atlantis-gcn-in disabled=no rule="accept;"
add chain=atlantis-gcn-in disabled=no rule="if (dst == 88.80.132.0/24) { accept; }"
add chain=atlantis-gcn-in disabled=no rule="if (dst == 88.80.133.0/24) { accept; }"
add chain=atlantis-gcn-in disabled=no rule="if (dst == 194.79.12.0/24) { accept; }"
add chain=atlantis-gcn-in disabled=no rule="if (dst == 194.79.13.0/24) { accept; }"
add chain=atlantis-gcn-in disabled=no rule="if (dst == 195.68.214.88/29) { accept; }"
add chain=atlantis-gcn-out comment=ITS disabled=no rule="if (dst == 0.0.0.0/0) { accept; }"
add chain=atlantis-gcn-out comment=ITS disabled=no rule="if (dst == 85.118.94.0/24) { accept; }"
add chain=atlantis-gcn-out comment=ITS disabled=no rule="if (dst == 85.118.95.0/24) { accept; }"
add chain=atlantis-gcn-out comment=ITS disabled=no rule="if (dst == 87.246.47.0/24) { accept; }"
add chain=atlantis-gcn-out comment=ITS disabled=no rule="if (dst == 87.246.48.0/24) { accept; }"
add chain=atlantis-gcn-out comment=ITS disabled=no rule="if (dst == 87.246.49.0/24) { accept; }"
add chain=atlantis-gcn-out comment=ITS disabled=no rule="if (dst in 172.16.0.0/12 && dst-len in 24..32) { accept; }"
add chain=atlantis-komudara-in disabled=no rule="if (dst == 88.80.132.0/24) { accept; }"
add chain=atlantis-komudara-in disabled=no rule="if (dst == 88.80.133.0/24) { accept; }"
add chain=atlantis-komudara-in disabled=no rule="if (dst == 194.79.12.0/24) { accept; }"
add chain=atlantis-komudara-in disabled=no rule="if (dst == 194.79.13.0/24) { accept; }"
add chain=atlantis-komudara-in disabled=no rule="if (dst == 195.68.214.88/29) { accept; }"
add chain=atlantis-komudara-out comment=ITS disabled=no rule="if (dst == 0.0.0.0/0) { accept; }"
add chain=atlantis-komudara-out comment=ITS disabled=no rule="if (dst == 85.118.94.0/24) { accept; }"
add chain=atlantis-komudara-out comment=ITS disabled=no rule="if (dst == 85.118.95.0/24) { accept; }"
add chain=atlantis-komudara-out comment=ITS disabled=no rule="if (dst == 87.246.47.0/24) { accept; }"
add chain=atlantis-komudara-out comment=ITS disabled=no rule="if (dst == 87.246.48.0/24) { accept; }"
add chain=atlantis-komudara-out comment=ITS disabled=no rule="if (dst == 87.246.49.0/24) { accept; }"
add chain=atlantis-komudara-out comment=ITS disabled=no rule="if (dst in 172.16.0.0/12 && dst-len in 24..32) { accept; }"
add chain=atlantis-gcn--ipv6-in disabled=no rule="accept;"
add chain=atlantis-gcn-ipv6-out disabled=no rule="if (dst == 2001:678:904::/48) { set gw 2001:678:904:1::1; accept; }"
add chain=zeuspack-in comment=ZeusPack disabled=no rule="if (dst == 109.160.12.0/24) { accept; }"
add chain=zeuspack-out disabled=no rule="if (dst == 0.0.0.0/0) { accept; }"
add chain=zeuspack-out comment=ITS disabled=no rule="if (dst == 85.118.94.0/24) { set bgp-communities 12:0; accept;}"
add chain=zeuspack-out comment=ITS disabled=no rule="if (dst == 85.118.95.0/24) { set bgp-communities 12:0; accept; }"
add chain=zeuspack-out comment=ITS disabled=no rule="if (dst == 87.246.47.0/24) { set bgp-communities 12:0; accept;}"
add chain=zeuspack-out comment=ITS disabled=no rule="if (dst == 87.246.48.0/24) { set bgp-communities 12:0; accept; }"
add chain=zeuspack-out comment=ITS disabled=no rule="if (dst == 87.246.49.0/24) { set bgp-communities 12:0; accept; }"
add chain=zeuspack2-in comment=ZeusPack disabled=no rule="if (dst == 109.160.12.0/24) { accept; }"
add chain=zeuspack2-out disabled=no rule="if (dst == 0.0.0.0/0) { accept; }"
add chain=zeuspack2-out comment=ITS disabled=no rule="if (dst == 85.118.94.0/24) { accept;}"
add chain=zeuspack2-out comment=ITS disabled=no rule="if (dst == 85.118.95.0/24) { accept;}"
add chain=zeuspack2-out comment=ITS disabled=no rule="if (dst == 87.246.47.0/24) { accept;}"
add chain=zeuspack2-out comment=ITS disabled=no rule="if (dst == 87.246.48.0/24) { accept;}"
add chain=zeuspack2-out comment=ITS disabled=no rule="if (dst == 87.246.49.0/24) { accept;}"
add chain=lukovitnet-in disabled=no rule="if (dst == 94.139.204.0/24) { accept; }"
add chain=lukovitnet-in disabled=no rule="if (dst == 94.139.205.0/24) { accept; }"
add chain=lukovitnet-in disabled=no rule="if (dst == 94.139.206.0/24) { accept; }"
add chain=lukovitnet-in disabled=no rule="if (dst == 94.139.207.0/24) { accept; }"
add chain=lukovitnet-in disabled=no rule="if (dst == 178.75.196.0/24) { accept; }"
add chain=lukovitnet-in disabled=no rule="if (dst == 178.75.197.0/24) { accept; }"
add chain=lukovitnet-in disabled=no rule="if (dst == 178.75.198.0/24) { accept; }"
add chain=lukovitnet-in disabled=no rule="if (dst == 178.75.199.0/24) { accept; }"
add chain=lukovitnet-in disabled=no rule="if (dst == 85.11.152.0/24) { accept; }"
add chain=lukovitnet-in disabled=no rule="if (dst == 85.11.153.0/24) { accept; }"
add chain=lukovitnet-in disabled=no rule="if (dst == 85.11.154.0/24) { accept; }"
add chain=lukovitnet-in disabled=no rule="if (dst == 85.11.155.0/24) { accept; }"
add chain=lukovitnet-out disabled=no rule="if (dst == 0.0.0.0/0) { accept; }"
add chain=lukovitnet-out comment=ITS disabled=no rule="if (dst == 85.118.94.0/24) { accept; }"
add chain=lukovitnet-out comment=ITS disabled=no rule="if (dst == 85.118.95.0/24) { accept; }"
add chain=lukovitnet-out comment=ITS disabled=no rule="if (dst == 87.246.47.0/24) { accept; }"
add chain=lukovitnet-out comment=ITS disabled=no rule="if (dst == 87.246.48.0/24) { accept; }"
add chain=lukovitnet-out comment=ITS disabled=no rule="if (dst == 87.246.49.0/24) { accept; }"
add chain=dabnik-gcn-in disabled=no rule="set bgp-local-pref 120; accept;"
add chain=dabnik-gcn-out disabled=no rule="if (dst == 0.0.0.0/0) { set gw 87.246.47.17; accept; }"
add chain=dabnik-komudara-in disabled=no rule="accept;"
add chain=dabnik-komudara-out disabled=no rule="if (dst == 0.0.0.0/0) { set gw 85.118.94.101; accept; }"
Приемане на входящи маршрути (-in chains)
accept;→ Приема всички маршрути без допълнителни ограничения.if (dst == x.x.x.x/x) { accept; }→ Приема само определени префикси.if (dst in x.x.x.x/x && dst-len in Y..Z) { accept; }→ Филтрира по дължина на маската (CIDR).set bgp-local-pref 120; accept;→ Увеличава Local Preference за определени маршрути.
Филтриране на изходящи маршрути (-out chains)
if (dst == x.x.x.x/x) { accept; }→ Разрешава само определени мрежи да бъдат рекламирани.if (dst == x.x.x.x/x) { set bgp-path-prepend 3; accept; }→ AS Path Prepending за контрол на маршрутизацията.if (dst == x.x.x.x/x) { set bgp-communities 12:0; accept; }→ Добавяне на BGP community tags.if (dst == 0.0.0.0/0) { set gw x.x.x.x; accept; }→ Пренасочване на default route към конкретен gateway.
/ip firewall address-list
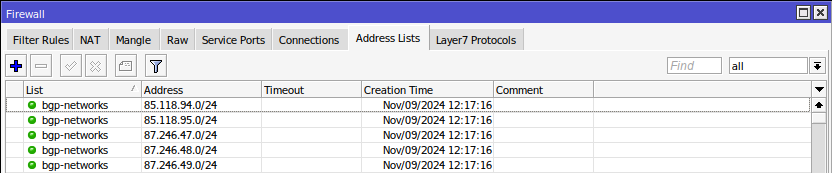
/ip firewall address-list
add address=85.118.94.0/24 disabled=no dynamic=no list=bgp-networks
add address=85.118.95.0/24 disabled=no dynamic=no list=bgp-networks
add address=87.246.47.0/24 disabled=no dynamic=no list=bgp-networks
add address=87.246.48.0/24 disabled=no dynamic=no list=bgp-networks
add address=87.246.49.0/24 disabled=no dynamic=no list=bgp-networksДобавя IP мрежи в /ip firewall address-list, като ги поставя в списъка bgp-networks.Мрежите в bgp-networks могат да се използват в BGP конфигурацията, за да се анонсират автоматично към BGP peer-ите.Параметри:
address=85.118.94.0/24→ IP мрежата, която се добавя в списъка.disabled=no→ Уверява се, че записът е активен.dynamic=no→ Това означава, че записът е статичен (не е добавен динамично от някой процес или правило).list=bgp-networks→ Определя, че тази мрежа принадлежи към списъка bgp-networks.
Каква е връзката с BGP?
В BGP конфигурацията виждаме следния ред:
/routing bgp connection
add as=47453 output.network=bgp-networks ...
.network=bgp-networks → Това означава, че всички мрежи от bgp-networks ще бъдат рекламирани към BGP peer-ите.

